Breach Writeup - THM Industrial Intrusion CTF (Task 3)
Breach was a pre-event task in the Industrial Intrusion CTF held by TryHackMe. It was a pretty easy challenge, which required nothing but very basic enumeration.
Following is the detailed write-up of the challenge, which breaks down the approach I used to crack the flag.
The problem statement was as follows:
This engagement aims to find a way to open the gate by bypassing the badge authentication system.
The control infrastructure may hold a weakness: Dig in, explore, and see if you have what it takes to exploit it.
Be sure to check all the open ports, you never know which one might be your way in!
According to the statement, we were supposed to bypass the infrastructure's authentication. We were also informed that all ports should be thoroughly checked.
-0x01: Enumeration:
Upon visiting the given address, the following web page was found.
I ran a TCP scan to look for open ports via Nmap.
The following ports were found on the target, along with the services running on them.
The 1880 port seemed interesting, hence I opened it in the browser.
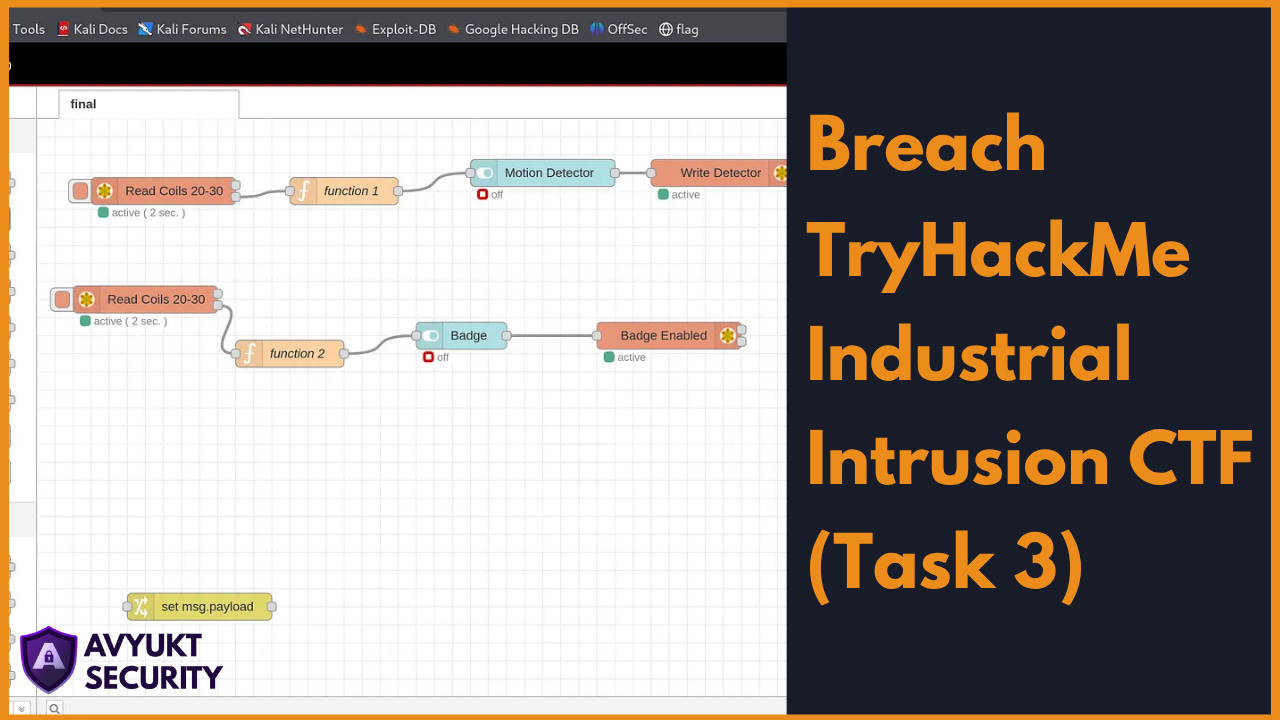
There was a Node-RED instance running on the port. I did a quick Google search regarding the same and found out that it was some sort of visual programming software which was used here to implement the badge authentication system.
I had no prior experience using a software like this yet I tried to work around the created logic to bypass the authentication, but nothing bore fruit.
I individually went on to enumerate all the open ports, but none of them proved to be of any use.
Port 8080 had a login page which was the one I had to bypass.
Then I thought of running a directory enumeration scan via Gobuster to look for possible directories on the port 1880.
I individually opened all the listed directories to look for possible flaws that could lead to the flag.
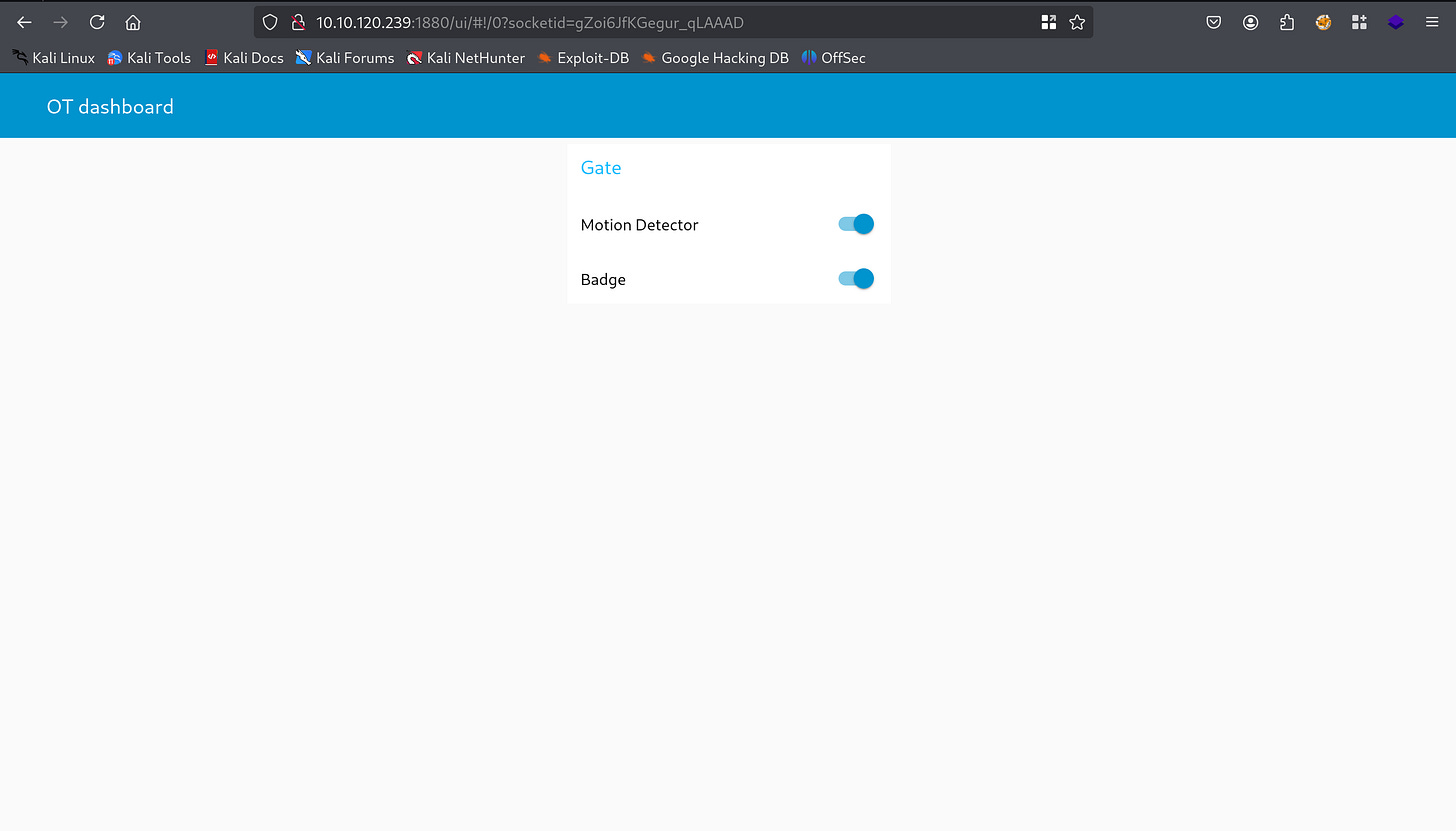
The /ui directory opened up the following web page which seemed interesting and very much in alignment with my approach.
I found two toggle switches, each for the Motion Detector and Badge. It was quite evident that turning them off would cease the functioning of the authentication system. So I did.
I rechecked the Node-RED dashboard and learnt that the detection system had been turned off as it was desired.
After that, I reopened the home page, and the authentication had been successfully bypassed as required by the objective of the task. The flag was successfully cracked!
This was the very first task of the CTF and probably one of the simplest ones. Anyone with fundamental enumeration skills could have easily navigated through this challenge without any hassle.
I hope you found this write-up helpful. Subscribe to Avyukt Security (it’s free) for more quality content on cybersecurity.
Happy Hacking!